Access to Blob storage using Managed Identity in Logic…
I am delighted to share the first guest post on my blog.
Nadeem Ahamed Riswanbasha is a cloud enthusiast and community contributor working for Serverless360 in India.
Please check out his Twitter and LinkedIn profile.
Access to Blob storage using Managed Identity in Logic Apps
By default, when we create a new blob storage container the level of public access will be set to “Private (no anonymous access)”. This is because to extend the security level of the blob container. Nevertheless, if the user wishes to set the level of public access to “container (anonymous read access to the container)” which allows accessing the file by anyone, then it can be modified at the time of creation.
Assume, the business use case needs a high level of security and wants to keep the container/blob more secure. In this case, there are a lot of ways to access the secured blob/container through proper authentication. One way of achieving authentication is through Managed Identity.
What is Managed Identity?
Managed Identity allows you to authenticate to Azure AD and access Azure resources. At the backend, the identity (credentials) will be managed and secured for you. The user doesn’t necessarily need to provide or rotate the secrets.
There are two types of Managed Identity
System-assigned
The lifecycle of a system-assigned identity is directly tied to the Azure service instance that it’s enabled on (Logic app here). So, if this Logic App is deleted, Azure automatically cleans up the credentials and the identity in Azure AD.
User-assigned
User-assigned managed identity is created as a standalone Azure resource i.e. Not tied to any service. So, it is the same as explicitly creating the AD app and can be shared by any number of services. Currently, Logic Apps only supports the system-assigned identity. Now, let us explore how to authenticate access to Azure Blob storage using Managed Identity in Logic Apps.
Enable managed identity in Logic Apps
First off, we need to enable the system-assigned identity in the logic app that you wish to access the blob storage through.
To do this, follow the steps below;
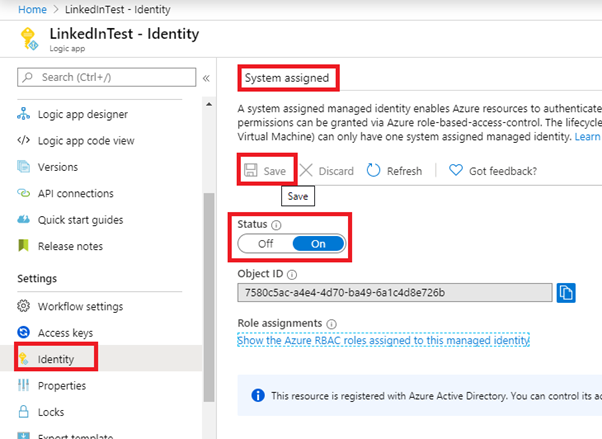
- Go to the logic app menu and select the identity option under settings
- A new window will be prompted under which switch the status option to ON and click Save.
Give managed identity access to Blob storage through RBAC
- Switch to the Azure Blob Storage container menu
- In the left pane, click on the Access control (IAM)
- Go to the Role Assignments option and click Add
- Now, a new blade will be opened on the right side of the window
- Fill in the details as follows;
Role – Storage Blob Data Contributor
Assign access to – Logic App
Select – <your logic app>


You can now see that the Logic App has been assigned as a Storage Account Contributor in the role assignment section.

Design the Logic App to access the Blob
Now, let us jump in and design the logic app to access the blob storage container or files into it. But remember, not all the trigger and actions of the logic app supports managed identity feature. Here is the list of triggers and actions that supports it.
- Now, let us head back to the logic app (here LinkedInTest) designer page
- Add a Recurrence trigger for the logic app with a defined interval of time
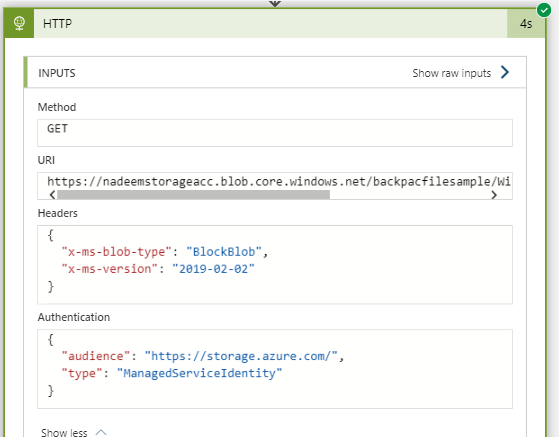
- Subsequently, add a new HTTP (it supports managed identity) action to the logic app
- In the HTTP action, fill the following fields as follow;
- Method – Get
- URI – <the URI of the blob>
- Headers –
- x-ms-blob-type: BlockBlob
- x-ms-version: 2019-02-02
- Authentication – Managed Identity
- Audience – https://storage.azure.com (this sets the scope to all of your storage accounts)

Test your Managed Identity enabled Logic App
Save the logic app and run it. You can now see in the run history of the logic app that blob content has been successfully accessed through managed identity authentication.
Wrap-up
In this blog, we have seen how to access blob using a system-assigned managed identity in the Logic Apps.
On enabling the logic apps managed identity, an AD app gets created with the same name as that of the azure service (here LinkedInTest, logic app) in Active directory, you can check it in Enterprise Application.
Hope you enjoyed reading this article. Happy Learning!


8 COMMENTS
I Passed the Exam thanks https://www.pass4surexams.com/
I have read your article carefully and I agree with you very much. This has provided a great help for my thesis writing, and I will seriously improve it. However, I don’t know much about a certain place. Can you help me? https://www.gate.io/id/signup/XwNAU
Thanks! Very helpful!
Hi Sofyan,
Did you ever resolve the put request content issue here?
Kind Regards,
Hi Sofyan,
Did you ever resolve the put request content issue here?
Kind Regards
One point … you have “Audience – https://storage.azure.com (this sets the scope to all of your storage accounts)” whereas your screen shot of the run history shows the audience as https://storage.azure.com/ i.e. a trailing forward slash. Which is it meant to be?
That said, I’ve tried it both ways and can’t either to work 🙁
Get an error
Server failed to authenticate the request. Make sure the value of Authorization header is formed correctly including the signature
Authentication scheme Bearer is not supported in this version
how do i do a put request .
I am able to get data content but what if i want to upload a file to blob how do i format my file content
Excellent and really useful article … many thanks for sharing
Comments are closed.