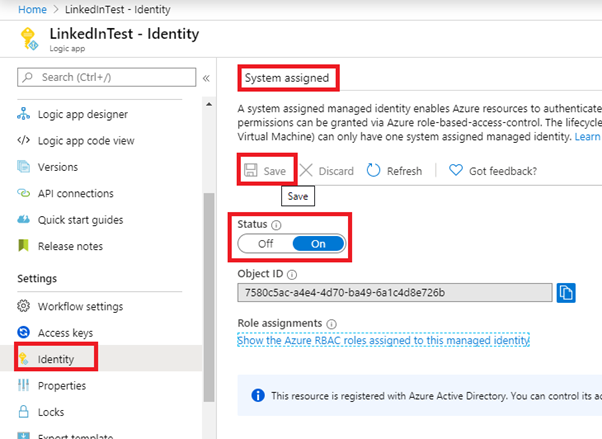
Azure
Azure
Azure spring clean 2020
Azure spring clean is a community initiative where the idea is to convey best practices and lessons learned managing Azure. During February 2020 we will have a broad selection of blog posts and videos on Real-world scenarios and solutions from the community. Covering topics like Azure Monitor, policies, and cost management.
The first post goes online on February 3.
| Date | Article | Contributor | Category |
|---|---|---|---|
| 03/02/20 | Azure RBAC – Best Practices | Alan Kinane | Azure Foundations |
| 04/02/20 | Azure Policy for AKS | Sam Cogan | Azure Policy |
| 05/02/20 | Monitoring Containers on Azure with Windows Admin Center | Dave Rendón | Azure Monitor |
| 06/02/20 | How to use Tags to organize your Azure resources | Wim Matthyssen | Azure Foundations |
| 07/02/20 | Azure Governance – Best Practises | Amine Charot | Azure Foundations |
| 10/02/20 | Nailing your Naming Convention with Azure Policy | Matt Browne | Azure Foundations |
| 11/02/20 | Azure Cost Management – Best Practises | Sarah Lean | Azure Cost Management |
| 12/02/20 | Protect your network resources with Azure Firewall | Luis Beltran | Azure Security Principles |
| 13/02/20 | Monitoring Azure Site Recovery | Karel De Winter | Azure Monitor |
| 14/02/20 | Using Azure Advisor to baseline your platform | Sam Hodgkinson | Azure Foundations |
| 17/02/20 | Using Azure Resource Graph To Assess Your Azure Environment Quickly & Efficiently | Jack Tracey | Azure Foundations |
| 18/02/20 | Azure Monitor – Best Practices for Sanity | Kam Salisbury | Azure Monitor |
| 19/02/20 | Azure Storage and Backup Lifecycle Best Practices | Dwayne Natwick | Azure Foundations |
| 20/02/20 | How to Use and Monitor Azure Update Management | Vukasin Terzic | Azure Fundamentals |
| 21/02/20 | Azure Security: my top 10 best practises to make your tenant secure as possible | Shabaz Darr | Azure Security Principles |
| 24/02/20 | Simplify Large Scale Deployments with Azure Blueprints | Isham Mohamed | Azure Foundations |
| 25/02/20 | Azure Kubernetes Service (AKS) securing Clusters and Applications | Adil Touati | Azure Security Principles |
| 26/02/20 | Azure Monitor – Autoscaling Resources Based on Performance | Anthony Mashford | Azure Monitor |
| 27/02/20 | How to Avoid a Billing Shock With Azure Serverless Solutions | Stanislav Lebedenko | Azure Cost Management |
| 28/02/20 | Securing Your Azure Platform Web Applications | Tidjani Belmansour | Azure Security Principles |
Thanks to all the content creators, MVPs Joe Carlyle and Thomas Thornton for starting this!